Early on Friday 12 May, reportedly somewhere in Europe, someone opened an attachment in an email that quite literally went viral. This was the beginning of an outbreak spread via file-sharing networks, which resulted in over 10,000 organisations’ and 200,000 people’s computers in 150 countries being infected by the sinisterly named WannaCry software. By exploiting a weakness in unpatched versions of Windows, the rogue software encrypted files on the computers and demanded $300 in bitcoin for the key to unlock them. Whoever paid must be wondering how long they will be on hold on the hackers’ helpline.
It is reported that the hackers only managed to scam $30,000 before being stopped by an entrepreneurial young security researcher who noted a reference in the bug’s code to an unregistered domain name. This domain name, which the self-taught IT expert registered for under $11, acted as a kill switch, neutralising the software.
Worryingly, but unsurprisingly, there are already allegations of a second version of the bug circulating, possibly without this kill switch in the code. The origins of the attack are as yet unknown; however, Microsoft’s chief legal officer explained that the method was, insidiously, “drawn from exploits stolen from the National Security Agency … in the United States” and “provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem.”[1]
While the bug was disarmed before many ransoms were paid, it did cause significant disruption to businesses and public services globally. In the UK, 48 NHS trusts were hit, causing them to cancel and delay treatments. Renault halted production at several European sites. Deutsche Bahn reported “system failures”, FedEx experienced “interference” with its systems and MegaFon in Russia confirmed it had also been hacked. Many other businesses and public services reported similar issues and disruptions across the globe.
The sheer number of companies affected is perhaps an insight into the quality of global corporate IT systems – Microsoft had issued a patch to the vulnerability in March of this year – but it is also an indication of the extent of the challenge to update and protect critical systems and sensitive data from cyber attacks. For example, while it might be easy to update a computer terminal sitting on a desk in an office with the latest security patches, it is much less simple to protect a piece of hospital equipment or critical infrastructure that might be running a version of Windows that is no longer supported.
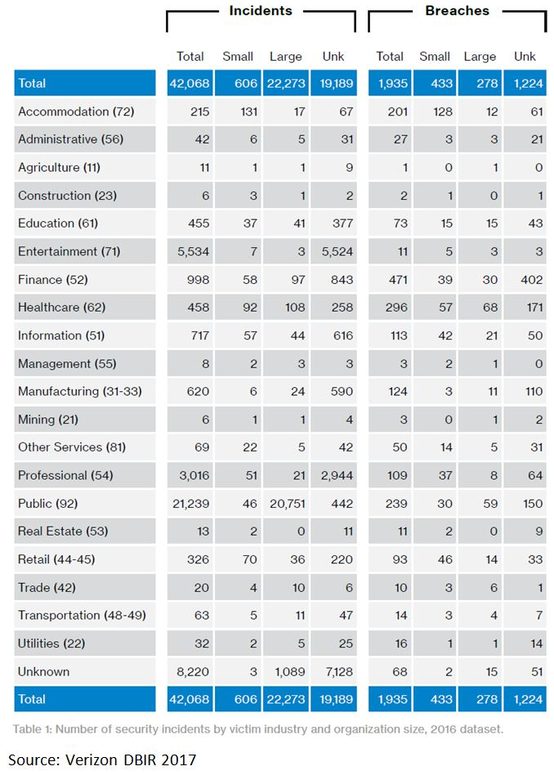
It is particularly interesting to note the breadth of the sectors that quickly discovered they were vulnerable. While it might be tempting to assume cyber risks are material to only a small few sectors, Verizon’s 2017 Data Breach Investigations Report (DBIR) confirms that cyber security is an issue that all companies should assess. Even if a company’s own systems are sufficiently protected, supply chains and service providers can create vulnerabilities – take for example the large number of incidents reported in the professional sector listed in the chart below.
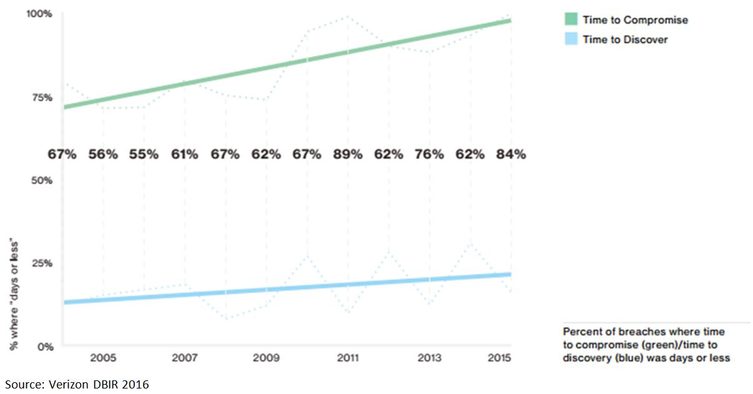
Our suspicion is that many businesses are woefully unprepared for this risk; PWC’s 2016 Cybercrime survey[2] found that only 37% of the organisations surveyed had a cyber incident response plan. To add to the issue, the hackers are able to act much more quickly than companies in defending themselves, and the trend appears to be getting worse. As the below chart shows, while the time taken for systems to be compromised is often very short, the time taken to discover the hacking is far longer.
Another piece of work by PWC found that while 61% of CEOs surveyed are concerned about cyber security, less than half of board members request information about their organisation’s preparedness for a cyber attack.[3] Research by EY revealed that 87% of board members and C-suite executives lack confidence in their organisation’s level of cyber security.[4] These statistics suggest a significant need to improve board-level, strategic understanding of cyber risks at companies; for this reason it is a key responsible investment research and engagement topic at Newton across all sectors.
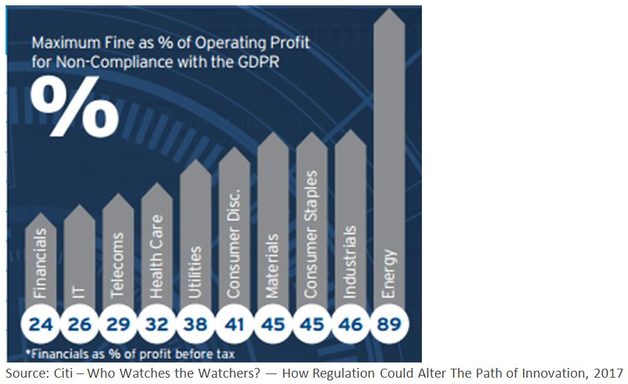
However, we believe this also presents investment opportunities in companies that can help businesses protect themselves. IDC assesses that the amount of digital data is doubling every year and by 2020 will reach 44 zettabytes (that’s 44 trillion gigabytes to us), much of which will be sensitive and need protecting.[5] The regulatory backdrop is moving quickly as well: for example, under the EU General Data Protection Regulation that comes into force in May 2018, companies will be liable for fines of up to 4% of annual global revenues for privacy and data breaches.
Stock picking in this area can be challenging given the rapidly evolving nature of the threats and the speed with which technologies can become redundant. However, our ‘security’ and ‘net effects’ investment themes provide us with vital perspective on this landscape, highlighting the attractive backdrop for demand for cyber protection, driven by the digitisation of data and the ‘connectivity of things’.
[1] https://blogs.microsoft.com/on-the-issues/2017/05/14/need-urgent-collective-action-keep-people-safe-online-lessons-last-weeks-cyberattack/#sm.0014wgev21eeafcxrc81u3jladv0g
[2] http://www.pwc.com/gx/en/services/advisory/forensics/economic-crime-survey/cybercrime.html
[3] https://www.pwc.com/gx/en/ceo-survey/2016/landing-page/pwc-19th-annual-global-ceo-survey.pdf
[4] http://www.ey.com/Publication/vwLUAssets/ey-global-information-security-survey-2016-pdf/%24FILE/GISS_2016_Report_Final.pdf
[5] https://uk.emc.com/leadership/digital-universe/2014iview/executive-summary.htm
Any reference to a specific security, country or sector should not be construed as a recommendation to buy or sell investments in those countries or sectors. Please note that holdings and positioning are subject to change without notice.






Comments